 Blazingly⚡ fast🚀 packet processing with DPDK
Blazingly⚡ fast🚀 packet processing with DPDK
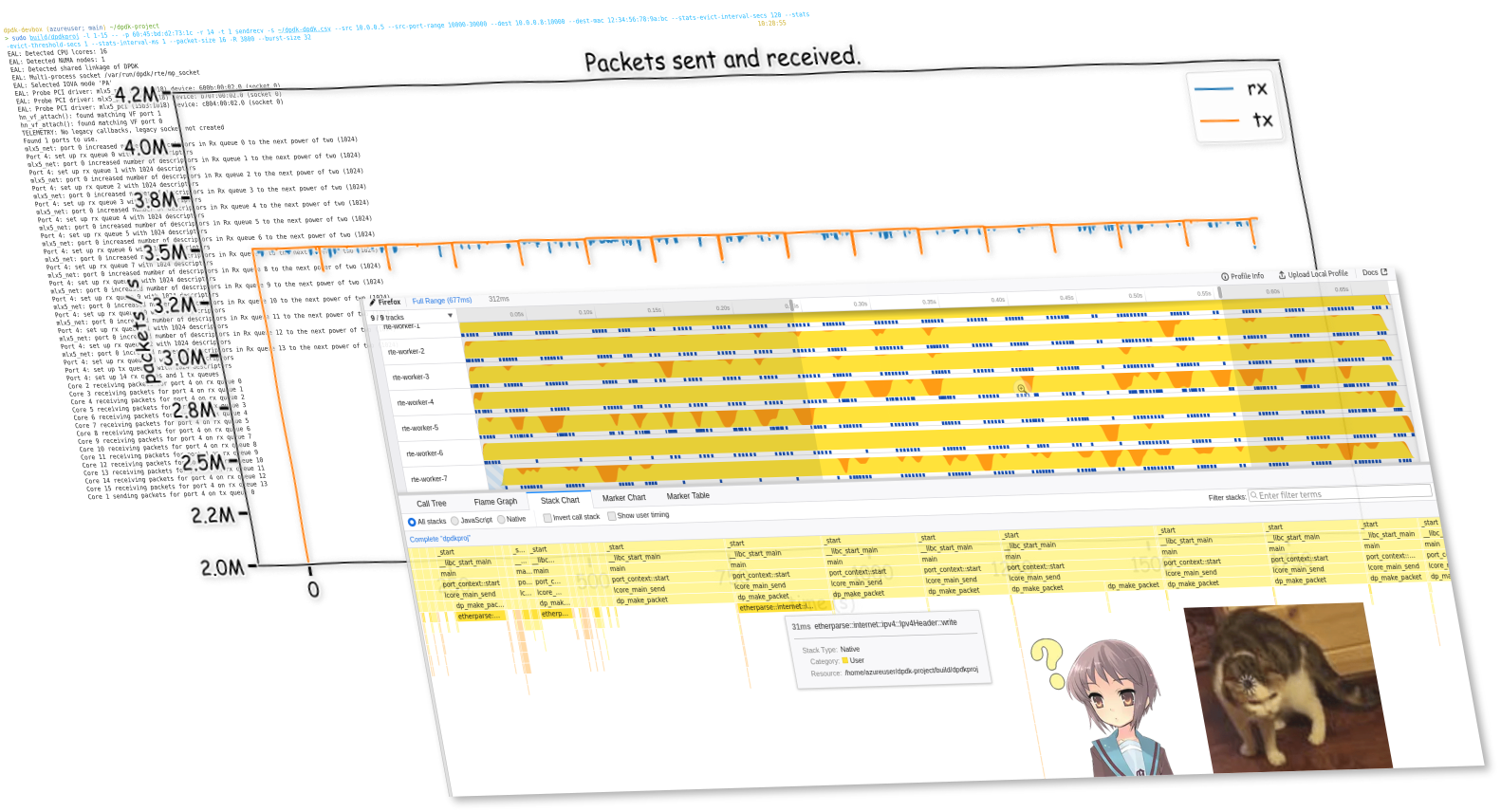
Recently at work I have been learning about this fancy framework we are using in a product with high-performance networking requirement — the Data Plane Development Kit (DPDK). It is a set of user-space NIC drivers and related utility libraries (like fast buffer pools or queues) that enables an application to bypass the Linux kernel's networking stack, and directly send and receive packets from the hardware...
For TLS, We require that the public key of web servers be signed by a publicly trusted CA in the form of a certificate bound to a domain name, and we trust that those CAs would only sign certificates after they have verified the server they are signing for controls the domain. However, there is no way for the public, or the site owner, to reliably know when a CA has breached this trust. We would be much safer if every valid certificate were discoverable by the public. Can we make that happen?